
Introduction to the Common Criteria(ISO/IEC 15408)
History and credentials
Responding to the need for mutual recognition of standardized security evaluation results in a global IT market, the CC represents the outcome of the pooled efforts of seven European and North American governmental organizations and the ISO to resolve the conceptual and technical differences found in their respective evaluation criteria and to replace them by an international standard.
In June 1999, this process led to the adoption of the CC Version 2.0 by the Joint Technical Committee 1 of the International Electrotechnical Commission of the International Organization for Standardization (ISO/IEC JTC 1). (The last CC Version 2.1 is an alignment revision enabling CC compliance to be equated with International Standard ISO/IEC 15408:1999 compliance.)
Content of the Common Criteria (ISO/IEC 15408)
So as not to rely solely on the assertions of the developers, many IT consumers require an analysis of the IT security of their IT products and systems. The CC focuses on the protection of assets with respect to three major issues: confidentiality, integrity and availability of data and resources.After having itemized the physical environment, the assets and the purpose of an IT product, analysts can identify threats and elaborate an organizational security policy to be able to state what are the assumptions about the environment and what are the security objectives of the product itself. From the identified security objectives, the next step of analysis is to derive the adequate set of security requirements for the product and security requirements for the environment, which, if met, will ensure that the product can meet its security objectives.
To permit comparability between the results of independent security evaluations, the Common Criteria unified methodology is based on two catalogues of common requirements: the security functional requirements and the security assurance requirements.
· The security functional requirements establish a set of functional components as a standard way of expressing all possible functional requirements for the product or system under evaluation, further referred to as “TOE” (Target of Evaluation).
· The security assurance requirements are a set of assurance measures applied to the TOE to give a statement on how high confidence can be that the security requirements are correctly fulfilled by the implementation.
Both catalogues of requirements are organized into the hierarchy of class – family – component to help consumers locate specific security requirements.
The use of the CC security requirements leads to two major distinct document constructs: the Protection Profiles (PPs) and the Security Targets (STs).
· PPs are designed for a whole category of TOEs such as smart cards or Public Key Infrastructures.
· STs are established for a single TOE and may, among other requirements, include compliance to one or more PPs.
With its evolutive library of approved PPs, the CC keeps on incorporating in its common set new constructs of known validity, allowing those responsible for IT Security to benefit from the prior experience and expertise of others.
The CC includes the rules to evaluate soundness and consistency of PPs and STs; these in turn provide the basis for evaluating a claimed ST compliant or PP compliant TOE.
Lastly, as an easy IT Security mutual recognition label, the CC security assurance requirements introduce the “Evaluation Assurance Levels”, with rates from 1 to 7 according to 7 predefined packages of security assurance components. Only the four first EALs are internationally and unconditionnally recognised.
Important: please, find out more about these first EALs at www.commoncriteria.org and have a look at the site index before answering the remaining questions.
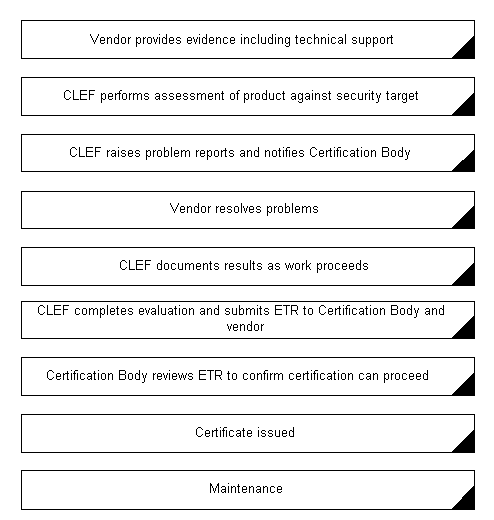
Flowchart of a Common Criteria certification in the UK
Definitions
CCRA : International recognition arrangement of May 2000 founding the CC certificationsCLEF: Commercial evaluation facilities
ETR: Evaluation technical report
The different steps
Chemin du Cornet, 15 7060 Soignies Belgique Entreprise 866-439-731 Ing 370-1149684-30






